What does ZEPTO infestation look like?
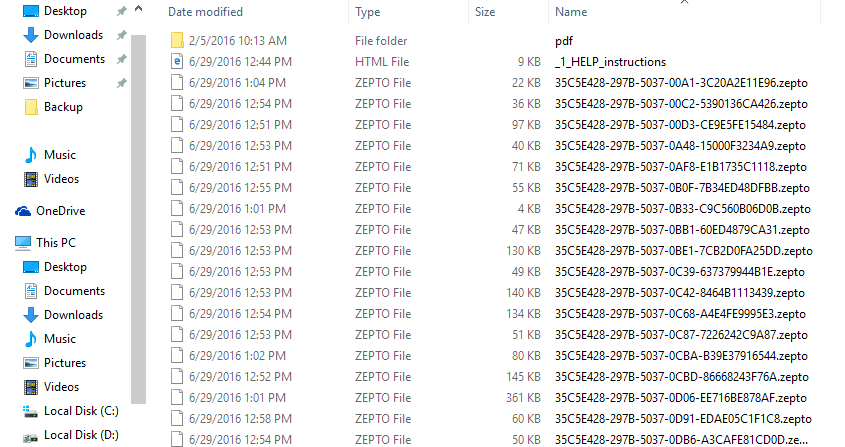
The ZEPTO ransomware is a relatively new comer to the ransomware scene.
Ransomware refers to a type of malware which renders computer files unusable by encryption. Theoretically the data is not destroyed as with older virusses, but simply encrypted: on payment of the ransom, a decryption key should then allow access to the data. Like with all terrorists and kidnappers, this is not always the case and news reports indicate several thousands of US Dollars paid, without recovering data.
Zepto characteristics include:
- Stealth
- Speed
- Aggression
- Total infestation
Comparison
Other ransomware strains such as Locky appear to be less aggressive in that it would typically exclude folders such as Windows, Program Files and the Desktop, allowing the computer to operate, but with no user access to the data.
Zepto on the other hand appears to take an all or nothing approach. Zepto infestations are total and at this point irreversible. There is no cure. The only solution is prevention.
Networks at risk
A common characteristic of all ransomware is the aggressive infestation of network devices. It is well known that ransomware readily replicates over mapped drives, but unmapped shares and Network Attached Storage (NAS) devices are also at risk.
Dropbox at risk
An additional threat of zepto to Windows Desktop Dropbox folders is that zepto will encrypt the content of the Dropbox folder.
This means that where a convenient Dropbox folder has been created for local data backup, a zepto infestation will typically render the files in the Dropbox folder useless.
In this way zepto poses a very real and present danger to small businesses using Dropbox as the only backup solution.
It is not yet clear to what extent zepto may replicate over shared Dropbox folders. Much like Pandora’s Box – opening an infected Dropbox folder may release the ransomware for a new wave of infestation.
MrBackup Solution
MrBackup offers a secure, remote data storage facility.
The snapshot approach taken by MrBackup means that the connection between the data source and the remote data server only exists for the duration of backing up the data. When a backup is not in progress, no connection exists between the local computer and remote host.
In addition, once the backup is received by the remote server, the data is compressed and stored in a secure operating system environment, where only user initiated processes are allowed, making it impossible for malware to propagate.
You need a MrBackup solution today!
