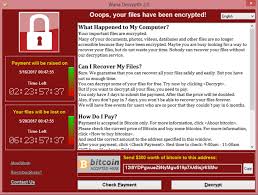
Warning: Extreme threat 15 May 2017
Updated.
If you see an image such as the screenshot above by The Verge, it means you have contracted the latest ransomware: WannaCry.
Full write ups appear here
- The WannaCry ransomware attack has spread to 150 countries
- Microsoft Just Took A Swipe At NSA Over The WannaCry Ransomware Nightmare
- What is WannaCry and how can it be stopped?
The following is known about WannaCry:
- It is the most aggressive ransomware to date
- It is Windows specific, targeting all versions of Windows.
- Unsupported versions of Windows and un-updated computers are at extreme risk
- It uses stealth and can silently spread over a network
- It uses a new exploit of the Microsoft SMB protocol
Why is WannaCry so difficult to stop?
While previous ransomware attacks were primarily distributed through email, WannaCry has one new feature which exploits known Microsoft vulnerabilities: it propagates over the Microsoft SMB protocol. Importantly the SMB protocol is used for File, directory, and share access authentication. This means that any file, folder or (unmapped) share on a computer can be used to propagate.
The SMB Protocol is central to the management and control of many Microsoft networks. WannaCry abuses these features to propagate and disable computers. Microsoft has already released patches to mitigate the extent of the WannaCry ransomware attack. Updated, supported versions of Windows have a better chance to resist the attack.
For more information on the Microsoft SMB Protocol, follow these links:
- How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server
- Microsoft SMB Protocol and CIFS Protocol Overview
In addition, TrendMicro informs that WannaCry spreads through embedded Dropbox URLs!
World wide impact
This strain of ransomware is so aggressive that it is being described as a Cyber Attack by The Telegraph Cyber attack: Stay away from GP surgeries unless urgent, amid fears of Monday meltdown. Microsoft considers the threat so severe that a special update has been released for the unsupported Windows XP operating system: Microsoft issues ‘highly unusual’ Windows XP patch to prevent massive ransomware attack. The Microsoft discussion with download links available here: Customer Guidance for WannaCrypt attacks.
Unsupported Windows Versions
Windows XP is unsupported.
Windows Vista is unsupported.
For more information on currently supported Windows versions, please see here Windows lifecycle fact sheet. Unsupported and out-of-date Windows versions are the weak link in stopping this ransomware attack.
Is anyone really still using Windows 95? Apparently the answer is Yes! According to several recent articles, such as this by Softpedia, the Pentagon Still Running Windows 95 and 98 on Critical Systems !
Prevention
Use supported versions of Windows with current updates. As with other ransomware threats, it appears that prevention is the only viable solution. The most effective prevention against a WannaCry infection consist of (a) an immediate Windows update, (b) anti-virus & anti-malware updates and scans, (c) awareness of the severity of the problem. As always, make sure you have a good working backup of your business critical systems.
Good luck, be safe
MrBackup
