February 2016: WARNING: a very powerful new strain of malware is currently in circulation.
Please note that Locky is a particularly nasty variant of the ransomware genre.
A crypto locker virus is not a single virus, but rather a type of virus that uses similar attack strategies. These viruses do not destroy data, but rather render the data useless until such time as a ransom is paid.
For more on ransomware, please follow this link:
http://en.wikipedia.org/wiki/Ransomware
The software modules that distributes Locky does not contain any typical malicious code, which makes it particularly hard to detect.
It appears that the primary means of infection is by way of email attachments. The email will typically display what appears to contain important information for your attention such as From: Accounts with Subject: Invoice. The email may appear authentic.
An example of such an email appears below.
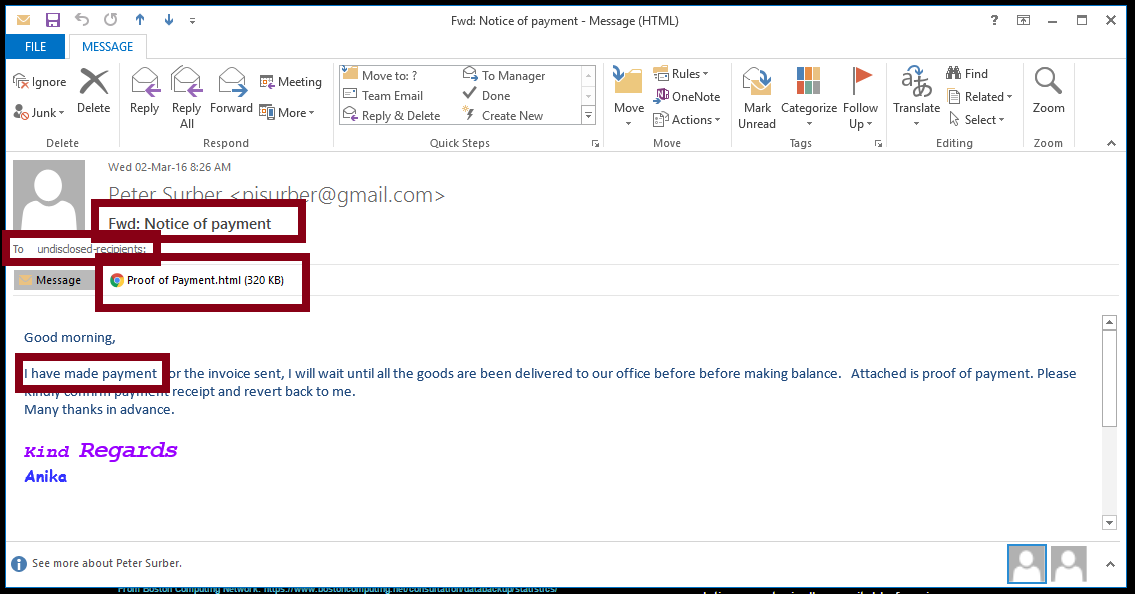
In this example, the Recipient was probably BCC’d. Note the content of the email, which appears to be an authentic message.
Upon opening the attachment, the Locky ransomware is downloaded to your computer, and activated.
It may lock the local computer within one to two hours and is known to spread via LAN connections.
At this time, it appears that user awareness may the single most important safety measure in preventing Locky infestation. If you do no recognize the sender, do not open the attachment.
In the event of an actual infestation, deleting the affected data and restoring a working backup appears to be the most viable solution.
Before you open email attachments, do the following:
- Check the name of the Sender. Do you recognize this name and email address?
- Check the Subject line. Are you expecting an email with such a subject from the sender?
- Read the message. Does the message match the subject line, does it come from a person you recognize?
- Do you expect an attachment? Do you recognize the attachment type?
If the answer to any of these questions is “No” then you should probably not open the email and the best precaution is simply to delete the email unread.
Based on the way Locky is spread, this type of risk is best classified as intentional malicious activity.
